For years, in addition to developing strategies to drive financial growth and secure a competitive edge amid rapidly evolving markets, business leaders have been facing a new and increasingly complex challenge: corporate security breaches.
These issues not only compromise business-critical data such as employee payroll and strategic planning, but also put confidential customer information and trust at risk.
To prevent exposure to these threats, organizations must implement well-defined security strategies and update their operational policies. These strategies must encompass tools, teams, and processes while maintaining a balance between protection priorities and the speed required by the business.
Below are key measures companies should adopt to protect against cyber intrusions and ensure data security:
Shield the Organization from External Threats
In the past, cybercriminals primarily targeted large enterprises and government entities. Today, however, small and mid-sized businesses have also become prime targets, including small e-commerce operations run on a single machine and large-scale digital marketplaces with hundreds of endpoints and thousands of users.
According to the Edelman Privacy Risk Index, which surveyed 6,400 executives across 29 countries, 81% believe their companies lack the training, expertise, or technology required for proper protection. Meanwhile, 73% report insufficient resources to address these challenges.
These statistics are alarming. Regardless of size, every company must rely on a solid security infrastructure.
Commonly deployed security solutions include antivirus software, firewalls, anti-spam filters, and network protection tools—all of which offer security features designed to safeguard all areas of the organization.
A wide range of solutions is available on the market, both as physical equipment (hardware) and virtual platforms (software) hosted in the cloud.
And when integrated, the security architecture makes it possible to apply protection policies across all control points, even without manual intervention to prevent attacks.
Without an adequate framework in place, it is impossible for a company to achieve robust shielding that enables it to defend itself and restore operations after a breach.
Keep an Eye on Employee Activity
To prevent cyberattacks and data leaks, management must prioritize prevention.
This involves implementing a strong security policy in conjunction with a reliable Data Loss Prevention (DLP) solution.
As security policies and DLP tools are deployed in business environments, it is equally important to raise employee awareness through meetings and training programs focused on the types of threats that could compromise company and customer data.
Phishing scams occur when attackers attempt to lure clicks by sending emails with seemingly relevant or important information, catching the employee’s attention.
Once the employee clicks the link, the embedded malware can quickly spread across the organization, causing financial damage that may even result in business closure.
Many organizations already use DLP systems that classify files by type; based on this classification, files may or may not be copied, attached, or modified.
For files classified as highly restricted, encryption is applied—creating a security layer that protects the data even in the event of theft.
Establish a Mobile Security Policy
According to Cisco, 9 billion mobile devices were connected to the Internet back in 2012.
And as the global adoption of smartphones and tablets continues to grow at a rapid pace, companies are becoming increasingly concerned about managing their use within the corporate environment.
That’s because cybercriminals may attempt to infect employees’ devices with malware that, once connected to a company network or computer, could jeopardize sensitive data and internal systems.
To mitigate this risk, organizations must also develop a mobile security policy that clearly outlines the risks associated with each type of device, as well as the procedures employees are expected to follow.
To ensure compliance with these policies and guidelines, managers need to establish strict monitoring practices and implement foundational technologies that help reduce data security risks and the misuse of mobile devices.
As a result, many companies are now adopting secure access systems in which no company data is stored on the mobile device itself. Instead, the information is accessed and viewed in real-time, without ever being downloaded to the device. This minimizes the risk of data leakage.
Monitor and Limit Access Rights
Have you ever taken a close look at your employees’ access levels?
Every organization should establish a clear access hierarchy, granting sensitive privileges only to trained professionals.
In many cases, using basic tools can already enhance information security—especially for small and micro businesses.
Larger companies often rely on centralized access management systems that monitor and control user access to ensure compliance with the company’s security policies.
This approach is essential for strengthening your protection measures and can help prevent serious issues down the line.
Invest in Encryption
Encryption is a complex and far-reaching concept, but it should be part of every organization’s daily operations.
By encrypting data exchanges within your company’s systems—or between your system and third parties—you ensure the confidentiality and integrity of the information, shielding it from unauthorized access.
In practice, encryption can be implemented in various ways, but at its core, it’s a set of techniques designed to protect data so that only the sender and the intended recipient can decode it.
It doesn’t “hide” a data exchange, but rather scrambles its contents in such a way that decoding is virtually impossible without the correct key.
Adopting systems that use encryption helps your company stay compliant with data protection regulations—such as Brazilian General Data Protection Law (LGPD)—and shields both personal and corporate information.
Rely on System Redundancy
Throughout our blog posts, we’ve often highlighted the importance of modern companies investing in IT infrastructure redundancy.
In other words, replicating critical systems and resources to ensure operational continuity.
This way, if a server, UPS device, router, or even an entire data center fails, a backup is immediately available to take over.
Redundancy has become a top priority for companies that simply can’t afford downtime in their systems.
Stay Aligned with Legal Compliance
As previously mentioned, it is crucial for your company to remain compliant with data protection regulations.
Laws such as Brazil’s LGPD and the General Data Protection Regulation (GDPR) in Europe, though relatively recent, are already in full effect and actively enforced by regulatory authorities.
In Brazil, non-compliance can lead to heavy fines and severe penalties.
Depending on the nature of the violation, your company may be fined up to 2% of its annual revenue, with a cap of R$50 million.
Moreover, in more serious cases, the company could be required to suspend its operations—potentially resulting in permanent closure.
But how can you ensure legal compliance?
The first step is to thoroughly assess your company’s data and IT infrastructure to identify gaps, vulnerabilities, and areas for improvement.
If your organization has never focused on this matter, rest assured: there are many actions to take.
And it is entirely possible to organize this compliance journey. Start by adopting best practices and implementing systems, tools, and software that simplify the process.
And that’s where Ascenty can support your business!
As the leading data center provider in Latin America, Ascenty has spent years building an infrastructure and operational model fully focused on protecting customer data.
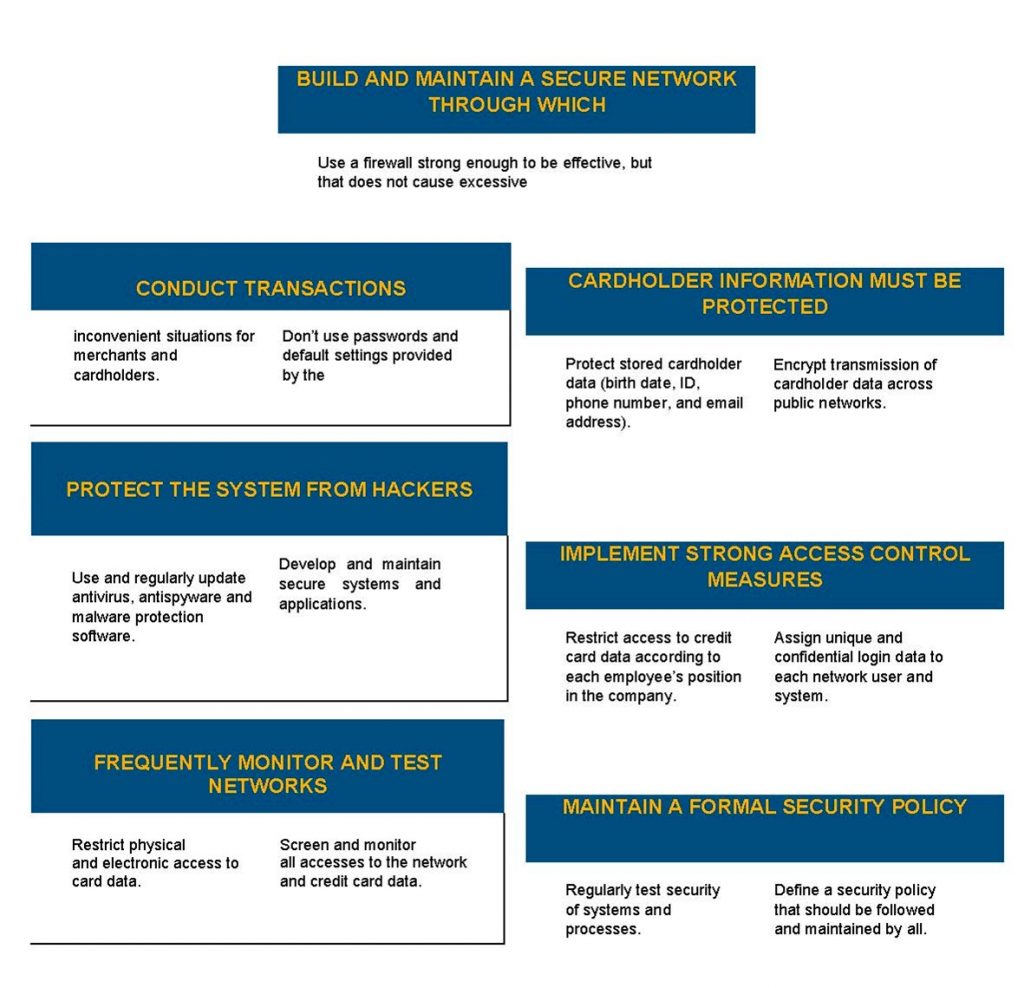
Certifications it holds that can attest to this include ISO 27001 and PCI-DSS Compliant.
Want to learn more about how Ascenty can support your business? Schedule a meeting with one of our specialists today!